Integrating SIEM + SOAR + XDR + GRC
For Enterprise and MSSP SOC teams to streamline their workflow, enhance threat detection and response, and to improve overall security, risk, and compliance posture.
Turn down the noise from alerts.
Simplify incident response process.
Quick time to value.
Improve Cost Efficiency
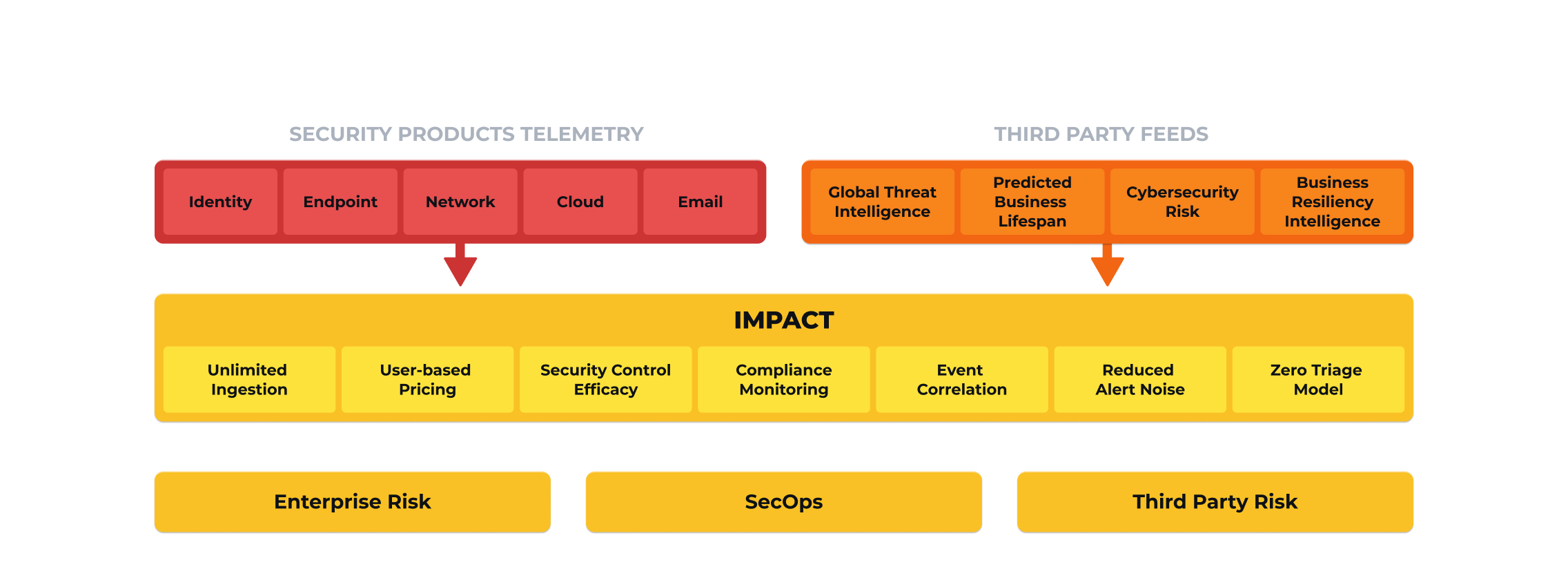
The Impelix IMPACT Platform eliminates one of your biggest challenges with legacy SIEM vendors – the high cost of data ingestion and storage and the inherent data compromise that it causes – with user-based pricing and one year of hot data retention.
Strengthen Your Security Posture
Our platform gives your security team visibility across your entire attack surface and offers real-time detection with automated (or one-click) response for seamless protection against advanced, persistent threats.
Reduce Compliance Risk
Knowing your company’s current cyber readiness, risk, and compliance is critical to assessing its posture and drives better business decisions. Impelix IMPACT offers continuous monitoring and comprehensive reporting in a streamlined service to make risk measurable and easily understood.

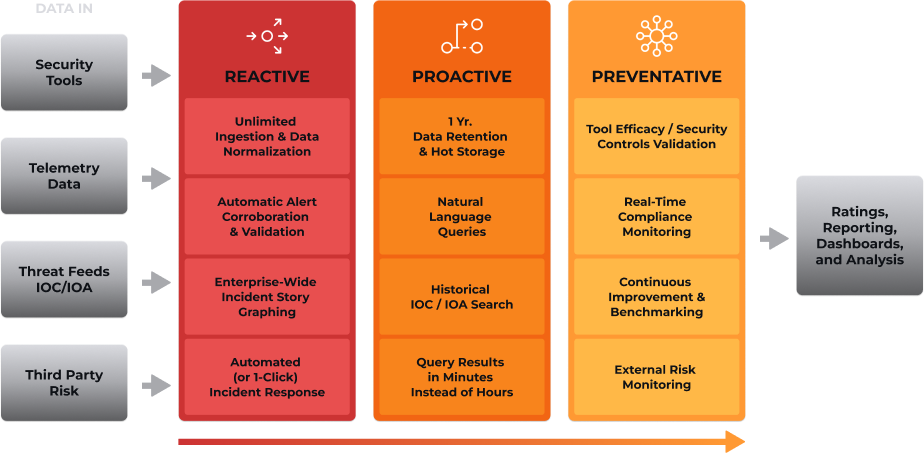
The Impelix IMPACT SOC Platform provides automated alert correlation and validation to address the alert noise and fatigue challenges that other solutions can’t address. The platform creates easy to understand enterprise-wide incident story graphing with automated incident responses to confidently enable your security and compliance teams to react quickly to attacks.
Proactive threat hunting and investigation is made simple through natural language queries and historical IOC and IOA searches. And unique to the Impelix IMPACT platform, integrated real-time compliance monitoring allows for continuous improvement, external risk monitoring, and tool efficacy for security controls validation.
We have a solution to address your needs
For Security Operations Analysts
Easy-to-Use AI-powered SecOps Automation
The Impelix Impact SecOps platform expands your visibility across the entire attack surface and helps your security teams mitigate real threats faster and more reliably than your SIEM to create better security outcomes — all with cost-contained pricing based on employees, not data.
- Reduce the Noise and Focus on the Real Threats
- Rapidly Address Security Incidents
- Automated Event Correlation and Response
- Quantify and Remediate Your Risk from All Attack Vectors


For Risk and Compliance Auditors
Predictive Analysis of Third-party and Business Risk
The Impelix IMPACT Enterprise Risk platform delivers continuous monitoring of risk and readiness, combining outside-in and inside-out intelligence, across six key capabilities to produce comprehensive reporting with many use cases.
- Cyber Readiness
- Cyber Risk
- Operations Efficiency
- Compliance Readiness
- Tool Efficacy
- Third Party Risk
For MSSPs/VARs
Help Your Customers Increase Their Risk and Security Posture
SOC (Security Operations Center) platform can provide your customers these key capabilities:
- Alert management and Incident workflow
- Threat detection and Incident response
- Threat mitigation and hunting
- Security automation and incident management
- Real-time compliance monitoring and management
- Security analytics and forensics analysis


For Executives
The Right Tool Will Save You Time and Money and Help Your Team
A modern security operations center (SOC) can provide many benefits for your organization. With the right SOC platform in place, you can be better prepared to face the challenges of the ever-changing security landscape and your enterprise risk and compliance to important regulations, including:
- Address your limited staff resources and skills
- Save money on data ingestion and data storage
- Insight into overlapping tool efficacy and what to do about it
- Understand your ratings on compliance and third-party risk