
We’ve been a distributed workforce at Impelix since our founding over a decade ago. This work-from-anywhere model created unique security gaps for us to mitigate. Many of them still lie in wait for companies now going 100% WFH. In my “Hidden Security Gaps For Remote Work” series, I’m sharing how we overcame them. Part one covered identity. Now, for part two, I’m investigating the endpoint …
A Rise in Off-Network Risk
With the sudden and dramatic shift from our normal office commute to a work-from-home environment, significant new challenges have sprung up. How do you maintain the same level of endpoint security when all your assets are now off-network? Being off-network has dramatically increased the attack surfaces of most organizations, making them ripe targets for bad actors. Across many of our clients, we have seen a dramatic uptick in phishing scams, ransomware and malware attempts.
Across many of our clients, we have seen a dramatic uptick in phishing scams, ransomware and malware attempts.
How can we combat this barrage of attacks?
Endpoint: The First Line of Defense
The first line of defense would be securing the endpoint. Endpoint protection comes in many flavors, but for the purpose of this post, I’ll focus on two: Next-Generation Antivirus (NGAV) and Endpoint Detection and Response (EDR).
So you may be asking yourself, what is the difference between NGAV and EDR? Aren’t both describing the same thing? They’re both ice cream, sure, but they’re different flavors. I’ll show you the differences in “taste” and why you need to combine both to serve up a “Defense in Depth” swirl.
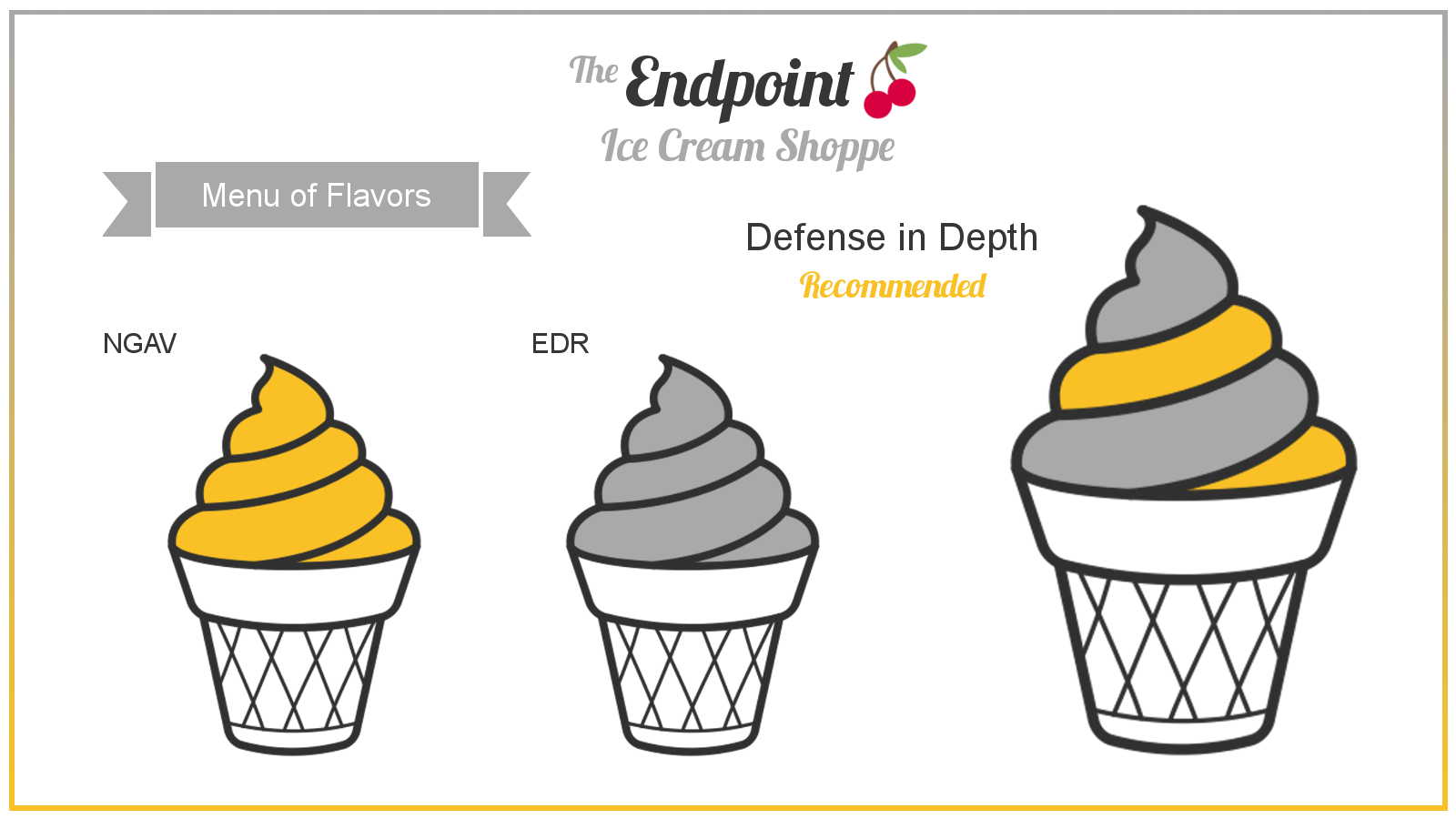
Next-Generation Antivirus
As the name suggests, it takes the concept of antivirus—with which all of us are familiar and have been using for 20+ years—and brings the technology into the 21st century.
What makes it “Next Generation”? It’s the enhancements in detection and prevention. The legacy antivirus engines used virus definition files that included signatures of known bad behaviors. Unfortunately, signature-based antivirus engines weren’t designed to handle the type of malware of today like polymorphic or multi-stage, just to name a couple.
The biggest advantage NGAV brings is the ability to identify both known and, more importantly, unknown malware and prevent it from causing any damage.
NGAVs use additional techniques to detect and prevent malware compared to legacy antivirus engines. Many will incorporate some combination of artificial intelligence, behavioral detection, machine learning algorithms, and exploit mitigation. The biggest advantage this brings is the ability to identify both known and, more importantly, unknown malware and prevent it from causing any damage.
Endpoint Detection and Response
If NGAV is capable of identifying and preventing known and unknown malware, doesn’t that mean the endpoint is secure? Not exactly. The answer is yes, but … there is still risk. If you notice, NGAV only talks about malware and preventing malware. What about all the other ways that an endpoint can be compromised? This is where EDR comes in.
EDR can secure the endpoint above and beyond just malware-based attacks. It’s ability to analyze different types of tactics and techniques from the bad actor’s actions provide an additional layer of security to the endpoint. EDR can detect and prevent actions like lateral movement, privilege escalation, and command and control communication to name a few.
With the additional capabilities, you get extra benefits (think sprinkles on top of your ice cream). Those can include:
- Process-level activity visibility
- File-level activity visibility
- Stitching of related attack activities
- Containment of host (with remote response capabilities)
Complete Endpoint Security: A Swirl of NGAV & EDR
If you are currently using a legacy antivirus solution, I implore you to upgrade to an endpoint solution technology that incorporates both NGAV and EDR capabilities. Remember: don’t pick a flavor, combine them.
A swirl of Defense in Depth for every endpoint
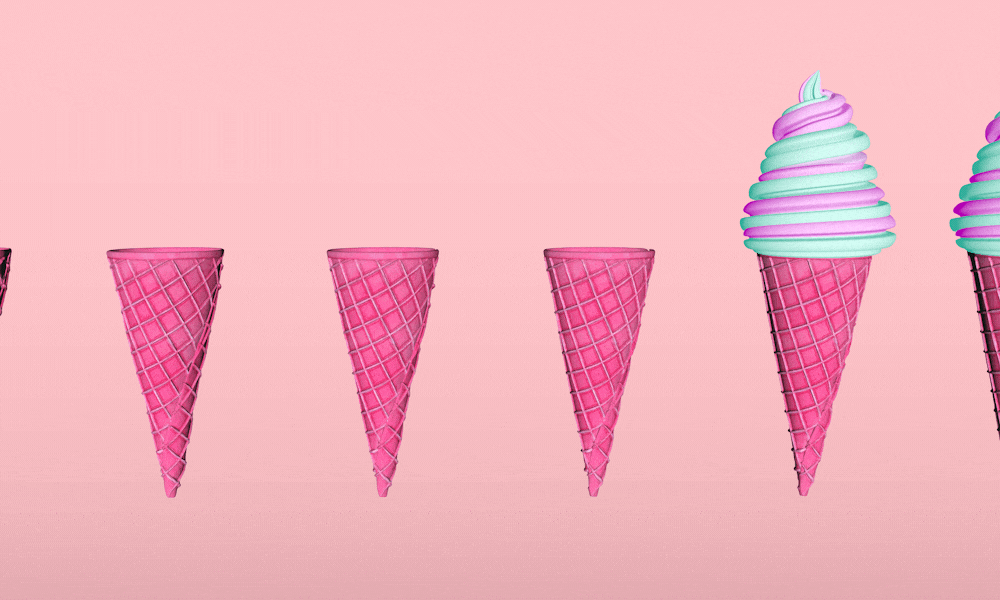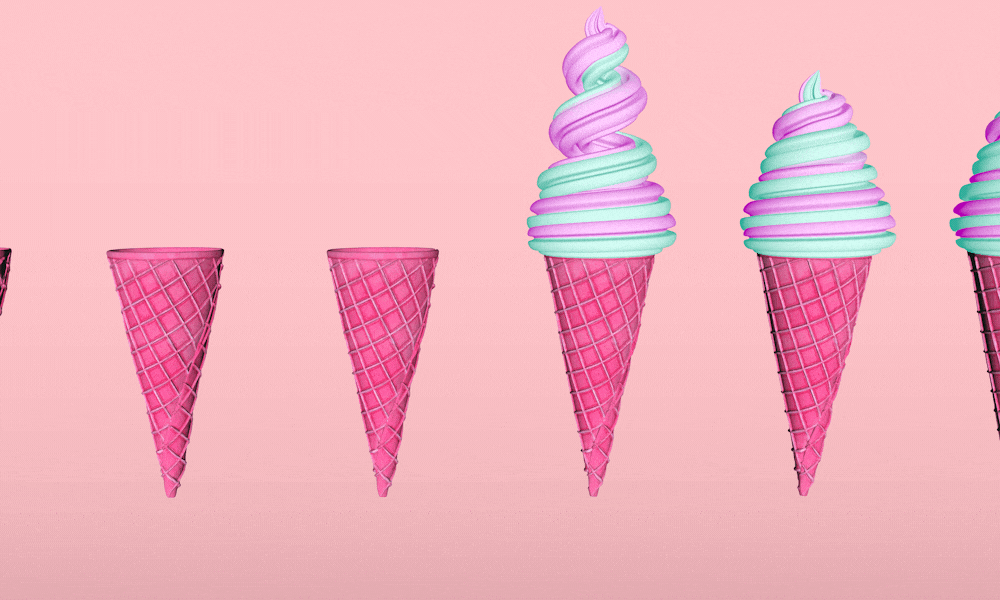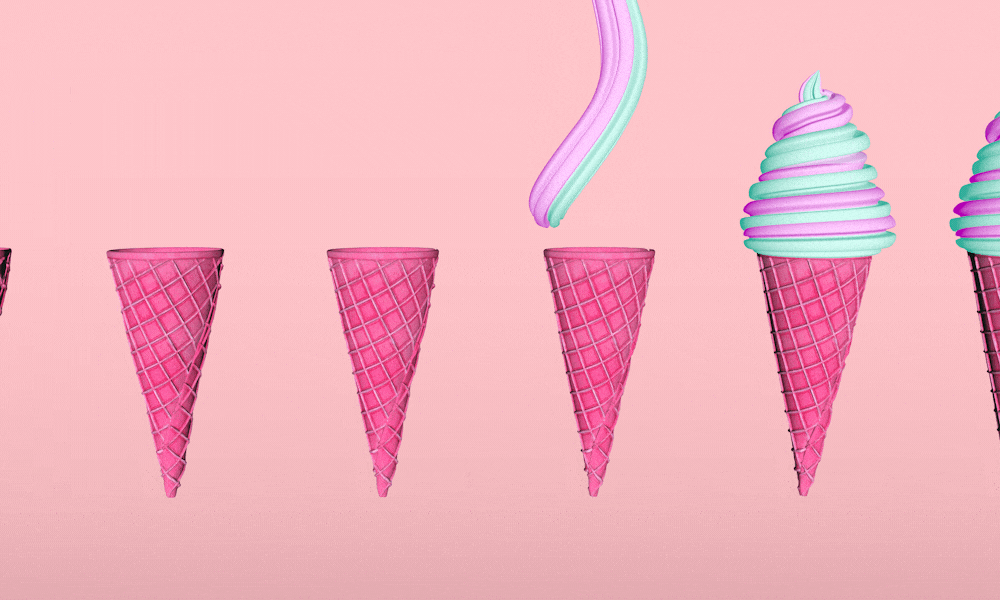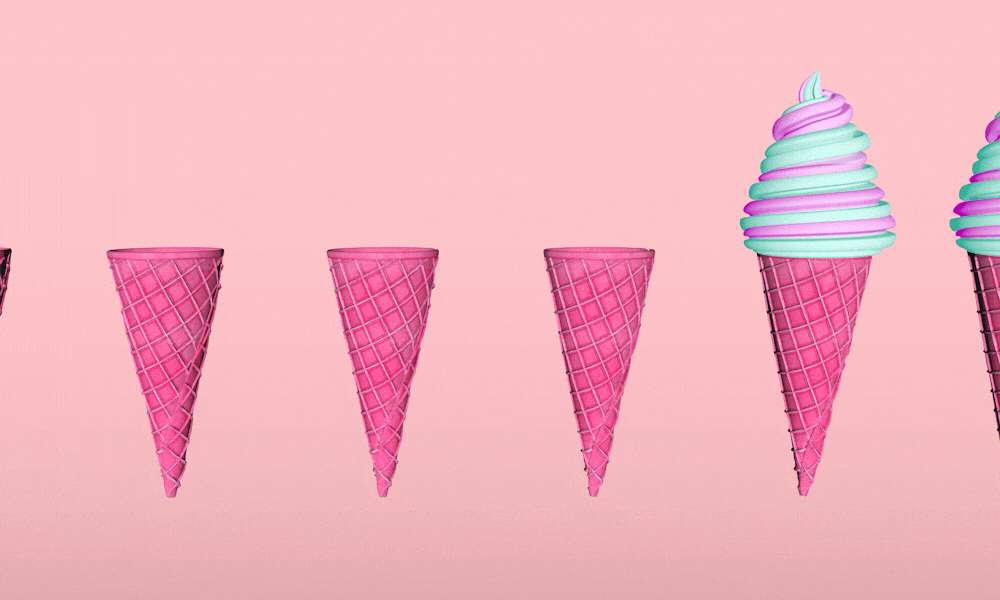
As you can see, a good endpoint security solution will combine the capabilities of NGAV and EDR to provide a comprehensive package to secure the endpoint—a Defense in Depth swirl. Many of the endpoint solutions incorporate additional functionalities, giving you more robust capabilities in visibility, intelligence, application and operating system vulnerability, and more.
A good endpoint security solution will combine the capabilities of NGAV and EDR to provide a comprehensive package to secure the endpoint—a Defense in Depth swirl.
I’d urge anyone who is already using these new endpoint security solutions to get very familiar with all the different features. There may be some hidden benefits that you’ve missed—possibly even displacing other tools you may have.
Emergency WFH Programs from CrowdStrike
If you are a current CrowdStrike customer, you can take advantage of new programs to help with the sudden shift to WFH offered at no additional cost: Burst Licensing Program and Falcon Prevent for Home Use.
Burst Licensing Program allows organizations to temporarily exceed their licensed endpoint count due to the immediate increased demand for remote workers. The Falcon Prevent for Home Use allows employees of CrowdStrike customers to install the NGAV agent onto their own devices.
Stay safe everyone … in the cyber world and the physical world.
Featured image from Vortech via Flickr
Ice cream GIF by @SummerBreak via Giphy
