In March, IT and security departments were forced to deploy a remote access solution nearly overnight, without the ability to assess beforehand the full impact of a 100% remote workforce.
Yet, despite a transition for workers to a new, productive normal, hidden security gaps linger—ones that may put your organization at risk. Previously, I wrote about Identity as part one and Endpoint as part two of this series.
Now in part three, I’ll look at the security gap created when employees are connected to the Internet while working from home.
The VPN Tradeoff
The default (and outdated) remote access solution deployed today is VPN. It provides a secure connection for your remote workers to access your internal resources. But what about internet or SaaS traffic? (Office 365, Salesforce, etc.)
You’re forced to make a tradeoff: do you choose performance or security? Which is really a choice about who gets to be happy …
You’re forced to make a tradeoff: do you choose performance or security?
If you choose performance via split-tunneling, your users will be happy. However, you won’t be, on account of restless nights worrying about the risk of their unfiltered internet access.
If you choose security via force tunneling, your users won’t be happy with the poor performance from backhauling their internet-bound traffic. Neither will your network team with the increased bandwidth consumption at the data center. And your nights will still be restless because of all the complaints.
It seems you’re damned if you do, damned if you don’t. Of course, that’s with yesterday’s solution, VPN. But what about tomorrow’s?
Heck Yes, We Can
Is it now possible for everyone to be happy? Can you really have your cake and eat it too with both security and performance? Heck yes, we can!

Solutions now exist that provide excellent security without compromising performance. These are based within the SASE concept and its core directive to move inspection engines to remote users, not the other way around, thereby inspecting traffic as close to the source as possible. In this model, it’s at the Service Edge that all security policies are enforced: Malware/Threat Protection, SSL Decryption, Data Security, and more.
Security policies enforced at the Service Edge
- Malware/Threat Protection
- SSL Decryption
- Data Security
- And more!
You get performance (no backhauling traffic) and security (NGFW functions at the Edge).
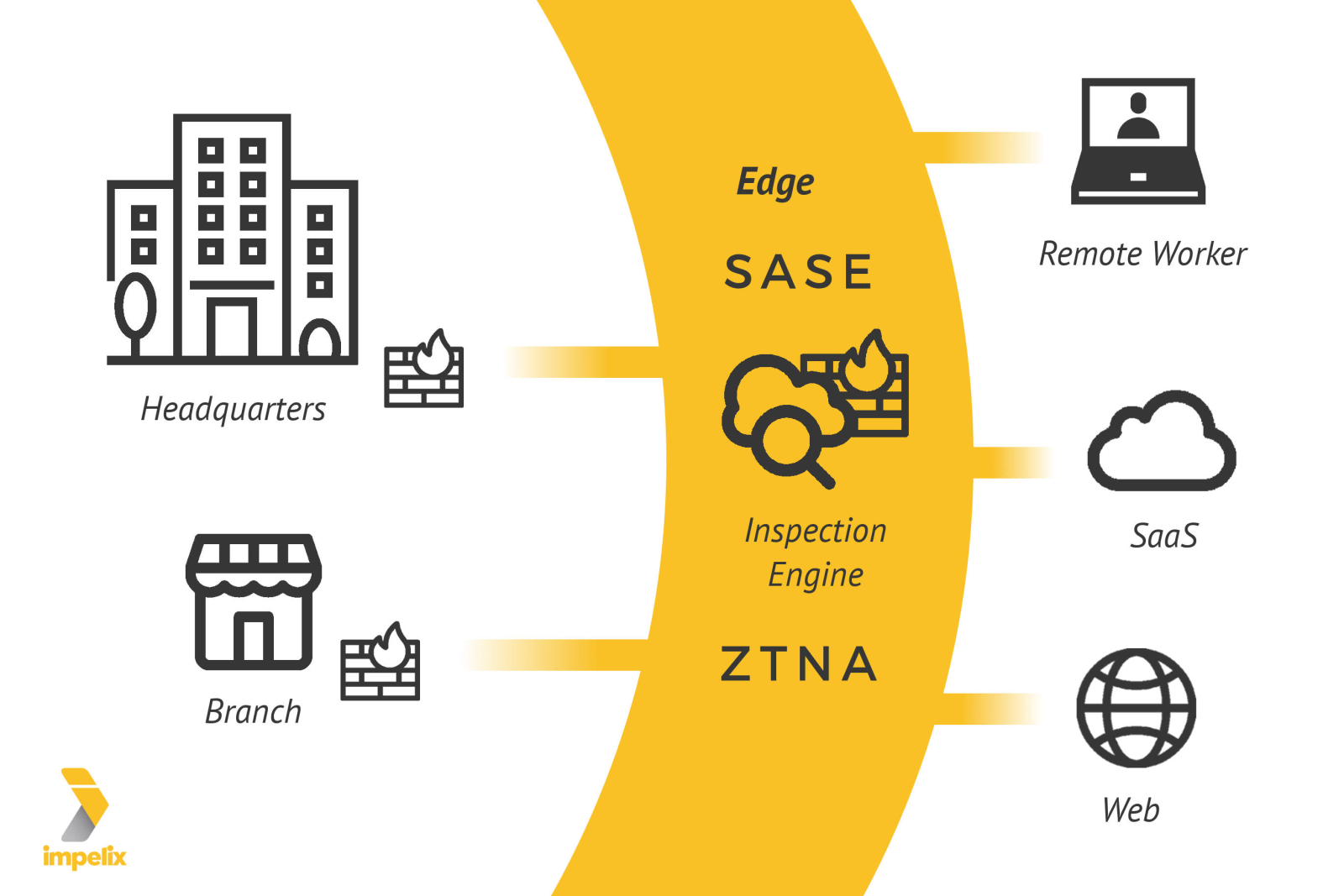
Private Access from the Edge
Here’s the icing on the cake: you can use this same Edge for private access to your corporate environment. What?!
Yes, this Edge also serves as your VPN gateway infrastructure. Say goodbye to your legacy VPN infrastructure. Say hello to the remote access VPN killer. These VPN killers can provide granular access down to the specific applications for each user. Can you say Zero Trust?
Say goodbye to your legacy VPN infrastructure. Say hello to the remote access VPN killer.
A SASE-based security infrastructure can provide secure access to the Internet for your remote users and a replacement of VPN connectivity that’s more agile and granular, accomplishing Zero Trust Network Access without any of VPN’s cumbersome infrastructure. Plus, because these next-gen solutions are cloud delivered, performing a proof of concept requires mere days, not weeks or months.
Goodbye, VPN
If you’ve continued to rely on VPN in the transition to WFH, you’ve most likely been forced to make a tradeoff. For many, it has come with increased risk to maintain an office-like experience for employees now working from their couches and kitchen tables. It doesn’t have to be that way.
Next-gen, cloud-based solutions are now available, capable of delivering a secure web gateway and ZTNA at the Edge by moving inspection engines out of the corporate data center to wherever remote users are located. So long, legacy tradeoff!
Have your cake. Eat it. Then lick the icing off your fingers while you wave goodbye to VPN.
